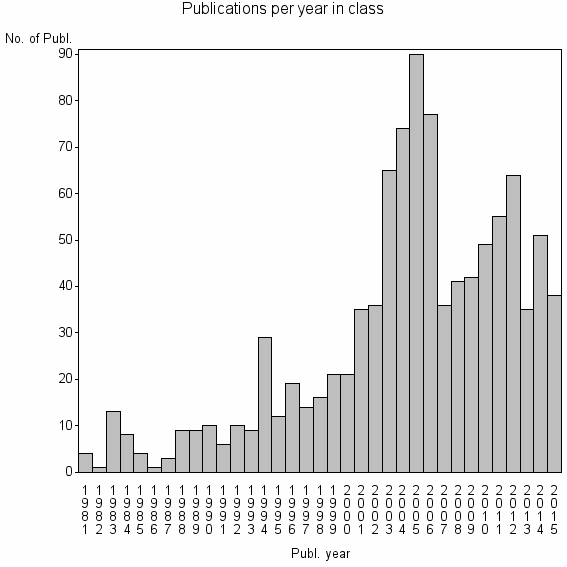
Class information for: |
Basic class information |
| ID | Publications | Average number of references |
Avg. shr. active ref. in WoS |
|---|---|---|---|
| 10330 | 1007 | 23.9 | 20% |
Classes in level above (level 2) |
| ID, lev. above |
Publications | Label for level above |
|---|---|---|
| 2639 | 3012 | PRIVACY CALCULUS//ACCESS CONTROL//INFORMATION PRIVACY |
Terms with highest relevance score |
| Rank | Term | Type of term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|---|
| 1 | CONTROLLED QUERY EVALUATION | Author keyword | 15 | 82% | 1% | 9 |
| 2 | ROLE BASED ACCESS CONTROL | Author keyword | 10 | 19% | 4% | 45 |
| 3 | RBAC | Author keyword | 8 | 15% | 5% | 50 |
| 4 | AUTHORIZATION MODELS | Author keyword | 6 | 80% | 0% | 4 |
| 5 | ROLE MAPPING | Author keyword | 5 | 60% | 1% | 6 |
| 6 | ROLE BASED ACCESS CONTROL RBAC | Author keyword | 5 | 32% | 1% | 14 |
| 7 | SECURE INTEROPERATION | Author keyword | 5 | 55% | 1% | 6 |
| 8 | DISTRIBUTED SYSTEM SECURITY | Author keyword | 4 | 67% | 0% | 4 |
| 9 | AUTHENTICATION AND AUTHORIZATION INFRASTRUCTURE | Author keyword | 4 | 75% | 0% | 3 |
| 10 | NESTOR | Address | 4 | 75% | 0% | 3 |
Web of Science journal categories |
Author Key Words |
Key Words Plus |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | RBAC | 17 | 72% | 1% | 13 |
| 2 | ACCESS CONTROL | 8 | 12% | 6% | 62 |
| 3 | ACCESS CONTROL MODEL | 7 | 44% | 1% | 12 |
| 4 | METHOD SCHEMAS | 6 | 100% | 0% | 4 |
| 5 | ACCESS CONTROL MODELS | 2 | 33% | 1% | 6 |
| 6 | TRUST MANAGEMENT | 2 | 15% | 1% | 14 |
| 7 | SCHEMATIC PROTECTION MODEL | 2 | 50% | 0% | 3 |
| 8 | AUTHORIZATION MODEL | 2 | 40% | 0% | 4 |
| 9 | INTEROPERATION | 2 | 33% | 0% | 5 |
| 10 | CONTROL MODELS | 2 | 27% | 1% | 6 |
Journals |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 3 | 12% | 2% | 22 |
Reviews |
| Title | Publ. year | Cit. | Active references |
% act. ref. to same field |
|---|---|---|---|---|
| DATABASE-SECURITY - RESEARCH AND PRACTICE | 1995 | 16 | 1 | 100% |
| Cloud authorization: exploring techniques and approach towards effective access control framework | 2015 | 0 | 5 | 60% |
Address terms |
| Rank | Address term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | NESTOR | 4 | 75% | 0.3% | 3 |
| 2 | CERIAS | 2 | 14% | 1.4% | 14 |
| 3 | INFORMAT EC | 2 | 40% | 0.4% | 4 |
| 4 | SECURE INFORMAT SYST | 2 | 14% | 1.1% | 11 |
| 5 | COORDINAMENTO PROGETTI INTERSETTORIALI | 1 | 100% | 0.2% | 2 |
| 6 | DIGITAL SECUR UNIT | 1 | 50% | 0.2% | 2 |
| 7 | MULTIMEDIA SERV SECUR CERTIFICAT | 1 | 100% | 0.2% | 2 |
| 8 | NCE UFRJ COMP | 1 | 100% | 0.2% | 2 |
| 9 | MATHS COMP | 1 | 24% | 0.4% | 4 |
| 10 | DATABASES INFORMAT SYST GRP | 1 | 40% | 0.2% | 2 |
Related classes at same level (level 1) |
| Rank | Relatedness score | Related classes |
|---|---|---|
| 1 | 0.0000267006 | CREDENTIAL VALIDATION SERVICE//ROLE BASED ACCESS CONTROLS//ACCESS CONTROL IN COLLABORATION ENVIRONMENTS |
| 2 | 0.0000144700 | TRUST NEGOTIATION//DISTRIBUTED PROVING//JAVA BASED MOBILE PHONE APPLICATION |
| 3 | 0.0000135722 | FEATURE INTERACTION//POLICY ANOMALIES//CALL PROCESSING LANGUAGE |
| 4 | 0.0000123119 | LERSAIS//WEB BASED SOCIAL NETWORKS//FERTIGATION SIMULATOR |
| 5 | 0.0000117140 | TRUSTED PERSONAL DEVICE//HIMALIS//LIBERTY ALLIANCE |
| 6 | 0.0000098967 | EDGE PREDICTION//FLEXRFID//HIPPOCRATIC DATABASES |
| 7 | 0.0000085776 | COMPETENCE DESCRIPTION//DATABASE EDUC//ADV E SERV KNOWLEDGE SOC UNIT |
| 8 | 0.0000075727 | BYTECODE VERIFICATION//PREVENT INFORMATION LEAKAGE//SEPARATION LOGIC |
| 9 | 0.0000073359 | USER HIERARCHY//KEY ASSIGNMENT//CRYPTOGRAPHIC KEY ASSIGNMENT |
| 10 | 0.0000068046 | CHAIR MOBILE COMMERCE MULTILATERAL SECUR//QUERY AUTHENTICATION//CSYSEC |