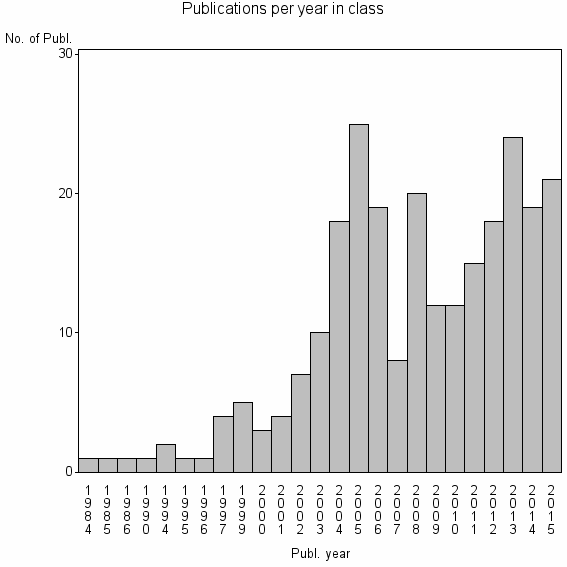
Class information for: |
Basic class information |
| ID | Publications | Average number of references |
Avg. shr. active ref. in WoS |
|---|---|---|---|
| 24787 | 252 | 24.6 | 21% |
Classes in level above (level 2) |
| ID, lev. above |
Publications | Label for level above |
|---|---|---|
| 1591 | 6600 | DIGITAL INVESTIGATION//COMPUTERS & SECURITY//INTRUSION DETECTION |
Terms with highest relevance score |
| Rank | Term | Type of term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|---|
| 1 | MTTSF | Author keyword | 4 | 75% | 1% | 3 |
| 2 | VULNERABILITY DISCOVERY MODEL | Author keyword | 2 | 67% | 1% | 2 |
| 3 | EMC APPROACH | Author keyword | 1 | 50% | 1% | 2 |
| 4 | CVSS | Author keyword | 1 | 30% | 1% | 3 |
| 5 | CODE SECURITY | Author keyword | 1 | 40% | 1% | 2 |
| 6 | MEAN TIME TO SECURITY FAILURE | Author keyword | 1 | 40% | 1% | 2 |
| 7 | ATTACK GRAPH | Author keyword | 1 | 10% | 3% | 8 |
| 8 | AIR SCI | Address | 1 | 33% | 1% | 2 |
| 9 | ADVERSARIAL MODELING | Author keyword | 1 | 50% | 0% | 1 |
| 10 | ATTACK PROCESS | Author keyword | 1 | 50% | 0% | 1 |
Web of Science journal categories |
Author Key Words |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | MTTSF | 4 | 75% | 1% | 3 | Search MTTSF | Search MTTSF |
| 2 | VULNERABILITY DISCOVERY MODEL | 2 | 67% | 1% | 2 | Search VULNERABILITY+DISCOVERY+MODEL | Search VULNERABILITY+DISCOVERY+MODEL |
| 3 | EMC APPROACH | 1 | 50% | 1% | 2 | Search EMC+APPROACH | Search EMC+APPROACH |
| 4 | CVSS | 1 | 30% | 1% | 3 | Search CVSS | Search CVSS |
| 5 | CODE SECURITY | 1 | 40% | 1% | 2 | Search CODE+SECURITY | Search CODE+SECURITY |
| 6 | MEAN TIME TO SECURITY FAILURE | 1 | 40% | 1% | 2 | Search MEAN+TIME+TO+SECURITY+FAILURE | Search MEAN+TIME+TO+SECURITY+FAILURE |
| 7 | ATTACK GRAPH | 1 | 10% | 3% | 8 | Search ATTACK+GRAPH | Search ATTACK+GRAPH |
| 8 | ADVERSARIAL MODELING | 1 | 50% | 0% | 1 | Search ADVERSARIAL+MODELING | Search ADVERSARIAL+MODELING |
| 9 | ATTACK PROCESS | 1 | 50% | 0% | 1 | Search ATTACK+PROCESS | Search ATTACK+PROCESS |
| 10 | CLOUD COMPUTING CIRCUMSTANCE | 1 | 50% | 0% | 1 | Search CLOUD+COMPUTING+CIRCUMSTANCE | Search CLOUD+COMPUTING+CIRCUMSTANCE |
Key Words Plus |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | COMMON VULNERABILITY | 4 | 75% | 1% | 3 |
| 2 | ALERT PRIORITIZATION | 1 | 40% | 1% | 2 |
| 3 | ATTACK GRAPHS | 1 | 15% | 2% | 6 |
| 4 | DAA SCHEME | 1 | 50% | 0% | 1 |
| 5 | AGENT SYSTEM | 0 | 33% | 0% | 1 |
| 6 | INTRUSION TOLERANT SYSTEMS | 0 | 33% | 0% | 1 |
| 7 | ANONYMOUS ATTESTATION SCHEME | 0 | 25% | 0% | 1 |
| 8 | E BANKING | 0 | 20% | 0% | 1 |
| 9 | COMPOSITE PERFORMANCE | 0 | 17% | 0% | 1 |
| 10 | BDD BASED ALGORITHM | 0 | 10% | 0% | 1 |
Journals |
Reviews |
| Title | Publ. year | Cit. | Active references |
% act. ref. to same field |
|---|---|---|---|---|
| The theory and practice in the evolution of trusted computing | 2014 | 0 | 3 | 67% |
| Model-based evaluation: From dependability to security | 2004 | 118 | 53 | 6% |
Address terms |
| Rank | Address term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | AIR SCI | 1 | 33% | 0.8% | 2 |
| 2 | COMP INFORMAT CONTENT SECUR | 1 | 50% | 0.4% | 1 |
| 3 | CONNECTED OBJECTS | 1 | 50% | 0.4% | 1 |
| 4 | IIG TELEMAT | 1 | 50% | 0.4% | 1 |
| 5 | INTEGRATED SECUR TECHNOL | 1 | 50% | 0.4% | 1 |
| 6 | LRI CNRS 8623 | 1 | 50% | 0.4% | 1 |
| 7 | MECH ENGN MAT PROGRAM | 1 | 50% | 0.4% | 1 |
| 8 | IND INFORMAT CONTROL SYST | 0 | 14% | 1.2% | 3 |
| 9 | BIOMED ENGN ELECT TELECOMMUN | 0 | 33% | 0.4% | 1 |
| 10 | BUSINESS ADM SOC | 0 | 33% | 0.4% | 1 |
Related classes at same level (level 1) |
| Rank | Relatedness score | Related classes |
|---|---|---|
| 1 | 0.0000218673 | INTERNATIONAL JOURNAL OF CRITICAL INFRASTRUCTURE PROTECTION//SUPERVISORY CONTROL AND DATA ACQUISITION SCADA SYSTEMS//TRUST CASE |
| 2 | 0.0000205695 | INTRUSION DETECTION//ALERT CORRELATION//INTRUSION DETECTION SYSTEM |
| 3 | 0.0000175110 | COMPUTERS & SECURITY//INFORMATION SYSTEMS SECURITY//IS SECUR |
| 4 | 0.0000133834 | INTERNET INFORMAT COMMUN//SOFTWARE FAULT ISOLATION//RANGE CHECKING |
| 5 | 0.0000126796 | REQUIREMENTS ENGINEERING//PROBLEM FRAMES//VIEWPOINTS |
| 6 | 0.0000114128 | SOFTWARE REJUVENATION//SOFTWARE AGING//OPTIMAL SOFTWARE REJUVENATION |
| 7 | 0.0000094268 | CAUSALITY GRAPH MODEL//EVENT CORRELATION//COGNIT ENGN PROGRAM |
| 8 | 0.0000093822 | DIRECTED HYPERGRAPHS//SUBSET GRAPH//SET THEORETIC ALGORITHMS |
| 9 | 0.0000083101 | IP TRACEBACK//DISTRIBUTED DENIAL OF SERVICE DDOS//DENIAL OF SERVICE |
| 10 | 0.0000082801 | TROMBONING//CELLULAR DIGITAL PACKET DATA CDPD//ARCHITECTURE TEAM |