Class information for: |
Basic class information |
| ID | Publications | Average number of references |
Avg. shr. active ref. in WoS |
|---|---|---|---|
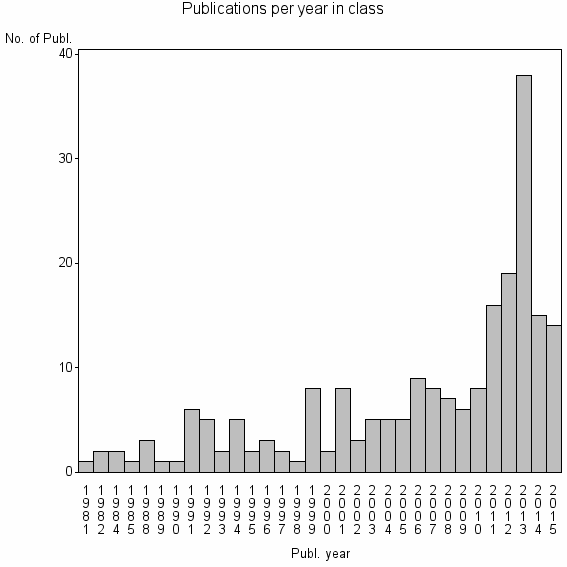
| 26264 | 213 | 52.8 | 12% |
Classes in level above (level 2) |
| ID, lev. above |
Publications | Label for level above |
|---|---|---|
| 1591 | 6600 | DIGITAL INVESTIGATION//COMPUTERS & SECURITY//INTRUSION DETECTION |
Terms with highest relevance score |
| Rank | Term | Type of term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|---|
| 1 | CYBER WAR | Author keyword | 4 | 38% | 4% | 8 |
| 2 | CYBER SECUR STUDIES | Address | 1 | 100% | 1% | 2 |
| 3 | CYBER WEAPONS | Author keyword | 1 | 50% | 1% | 2 |
| 4 | DEMAND FOR CLIMATE PROTECTION | Author keyword | 1 | 100% | 1% | 2 |
| 5 | IRREGULAR WAR | Author keyword | 1 | 40% | 1% | 2 |
| 6 | STRATEGIC THEORY | Author keyword | 1 | 40% | 1% | 2 |
| 7 | AFGHAN WAR | Author keyword | 1 | 50% | 0% | 1 |
| 8 | APPARATUSES OF SECURITY | Author keyword | 1 | 50% | 0% | 1 |
| 9 | ATTACKER DEFENDER GAME | Author keyword | 1 | 50% | 0% | 1 |
| 10 | BUSINESS CRIME | Author keyword | 1 | 50% | 0% | 1 |
Web of Science journal categories |
Author Key Words |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | CYBER WAR | 4 | 38% | 4% | 8 | Search CYBER+WAR | Search CYBER+WAR |
| 2 | CYBER WEAPONS | 1 | 50% | 1% | 2 | Search CYBER+WEAPONS | Search CYBER+WEAPONS |
| 3 | DEMAND FOR CLIMATE PROTECTION | 1 | 100% | 1% | 2 | Search DEMAND+FOR+CLIMATE+PROTECTION | Search DEMAND+FOR+CLIMATE+PROTECTION |
| 4 | IRREGULAR WAR | 1 | 40% | 1% | 2 | Search IRREGULAR+WAR | Search IRREGULAR+WAR |
| 5 | STRATEGIC THEORY | 1 | 40% | 1% | 2 | Search STRATEGIC+THEORY | Search STRATEGIC+THEORY |
| 6 | AFGHAN WAR | 1 | 50% | 0% | 1 | Search AFGHAN+WAR | Search AFGHAN+WAR |
| 7 | APPARATUSES OF SECURITY | 1 | 50% | 0% | 1 | Search APPARATUSES+OF+SECURITY | Search APPARATUSES+OF+SECURITY |
| 8 | ATTACKER DEFENDER GAME | 1 | 50% | 0% | 1 | Search ATTACKER+DEFENDER+GAME | Search ATTACKER+DEFENDER+GAME |
| 9 | BUSINESS CRIME | 1 | 50% | 0% | 1 | Search BUSINESS+CRIME | Search BUSINESS+CRIME |
| 10 | COUNTERDECEPTION | 1 | 50% | 0% | 1 | Search COUNTERDECEPTION | Search COUNTERDECEPTION |
Key Words Plus |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | OFFENSE DEFENSE THEORY | 1 | 50% | 0% | 1 |
| 2 | ESPIONAGE | 0 | 20% | 0% | 1 |
| 3 | MILITARY AFFAIRS | 0 | 20% | 0% | 1 |
| 4 | CYBERCRIME | 0 | 17% | 0% | 1 |
| 5 | ETHNIC HETEROGENEITY | 0 | 17% | 0% | 1 |
| 6 | HUMAN RIGHTS ACT | 0 | 17% | 0% | 1 |
| 7 | STUXNET | 0 | 17% | 0% | 1 |
| 8 | INFORMATION WARFARE | 0 | 14% | 0% | 1 |
| 9 | TRADE SECRET LAW | 0 | 13% | 0% | 1 |
| 10 | UK CIVIL CONTINGENCIES | 0 | 13% | 0% | 1 |
Journals |
Reviews |
| Title | Publ. year | Cit. | Active references |
% act. ref. to same field |
|---|---|---|---|---|
| SOLVING THE DILEMMA OF STATE RESPONSES TO CYBERATTACKS: A JUSTIFICATION FOR THE USE OF ACTIVE DEFENSES AGAINST STATES WHO NEGLECT THEIR DUTY PREVENT | 2009 | 7 | 4 | 75% |
| Computer network attack and the use of force in international law: Thoughts on a normative framework | 1999 | 25 | 8 | 25% |
| Cyber situational awareness - A systematic review of the literature | 2014 | 1 | 12 | 25% |
| Information Technologies, Meta-power, and Transformations in Global Politics | 2013 | 5 | 22 | 14% |
| Criminal proceedings after the Human Rights Act: The first year | 2001 | 2 | 2 | 50% |
Address terms |
| Rank | Address term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | CYBER SECUR STUDIES | 1 | 100% | 0.9% | 2 |
| 2 | CEBROWSKI INNOVAT INFORMAT SUPER | 1 | 50% | 0.5% | 1 |
| 3 | CHAIR INTERDISCIPLINARY STUDIES | 1 | 50% | 0.5% | 1 |
| 4 | COMP CRIME INTELLECTUAL PROPERTY SECT | 1 | 50% | 0.5% | 1 |
| 5 | JOINT TRANS CRIME | 1 | 50% | 0.5% | 1 |
| 6 | KNOWLEDGE DATA ENGN | 1 | 50% | 0.5% | 1 |
| 7 | PROGRAM ARMS CONTROL DISARMAMENT INT SECUR ACDI | 1 | 50% | 0.5% | 1 |
| 8 | PROGRAM LAW BEHAV | 1 | 50% | 0.5% | 1 |
| 9 | SECUR POLICY | 1 | 50% | 0.5% | 1 |
| 10 | CITIZEN | 0 | 20% | 0.9% | 2 |
Related classes at same level (level 1) |
| Rank | Relatedness score | Related classes |
|---|---|---|
| 1 | 0.0000119374 | MILITARY INNOVATION//MILITARY TRANSFORMATION//STRATEGIC STUDIES |
| 2 | 0.0000079919 | AMERICAN JOURNAL OF INTERNATIONAL LAW//COLUMBIA JOURNAL OF TRANSNATIONAL LAW//HARVARD INTERNATIONAL LAW JOURNAL |
| 3 | 0.0000079478 | KAMILA SHAMSIE//SLCR//SOCLAS |
| 4 | 0.0000066187 | COMPROMISE SET//IMPROVEMENT OF PRODUCTIVITY//INTERFACE ARCHITECTURES |
| 5 | 0.0000065721 | ENI//ANGLO PORTUGUESE RELATIONS//CRITICAL MAKING |
| 6 | 0.0000065349 | CYNODON DACTYLON CV 67//PANICUM MAXIMUM CV LIKONI//GILBERT TOBIN PUBL LAW |
| 7 | 0.0000065206 | BOUNDARY COMMISSIONS//BOUNDARY DEMARCATION//GEOSPATIAL INFORMATION SCIENCE |
| 8 | 0.0000059474 | COGNITIVE BOUNDARIES//FESTA//MCCALLUM |
| 9 | 0.0000057427 | COMPUTERS & SECURITY//INFORMATION SYSTEMS SECURITY//IS SECUR |
| 10 | 0.0000056801 | INFORMATIONAL CAPITALISM//PRODUSAGE//BLINDSPOT DEBATE |