Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
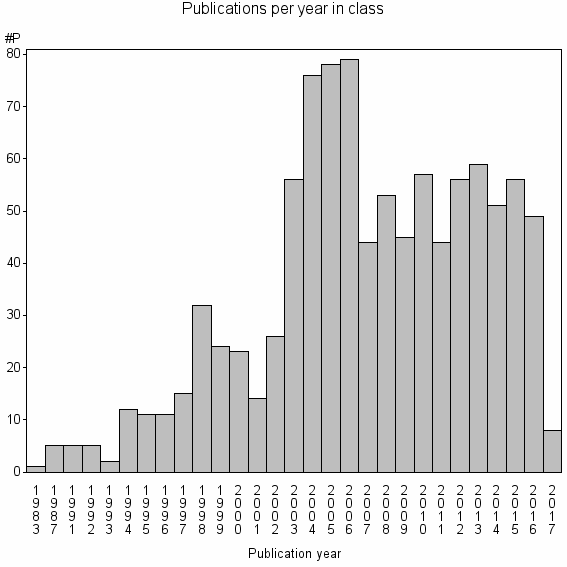
| 11246 | 997 | 33.0 | 24% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | REQUIREMENTS ENGINEERING | journal | 833956 | 8% | 34% | 80 |
| 2 | USE CASES | authKW | 592898 | 5% | 40% | 48 |
| 3 | GOAL MODELING | authKW | 476485 | 2% | 68% | 23 |
| 4 | GOAL ORIENTED REQUIREMENTS ENGINEERING | authKW | 465830 | 2% | 89% | 17 |
| 5 | SECURITY REQUIREMENTS | authKW | 445896 | 3% | 47% | 31 |
| 6 | PROBLEM FRAMES | authKW | 272399 | 1% | 68% | 13 |
| 7 | REQUIREMENTS ELICITATION | authKW | 218901 | 2% | 31% | 23 |
| 8 | SECURITY REQUIREMENTS ENGINEERING | authKW | 217781 | 1% | 89% | 8 |
| 9 | SECURITY ENGINEERING | authKW | 195985 | 2% | 40% | 16 |
| 10 | MISUSE CASES | authKW | 166737 | 1% | 78% | 7 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Software Engineering | 63780 | 58% | 0% | 580 |
| 2 | Computer Science, Information Systems | 22653 | 39% | 0% | 390 |
| 3 | Computer Science, Theory & Methods | 10595 | 29% | 0% | 285 |
| 4 | Computer Science, Artificial Intelligence | 3773 | 16% | 0% | 164 |
| 5 | Computer Science, Hardware & Architecture | 1812 | 8% | 0% | 78 |
| 6 | Logic | 277 | 1% | 0% | 12 |
| 7 | Engineering, Electrical & Electronic | 268 | 12% | 0% | 120 |
| 8 | Computer Science, Cybernetics | 199 | 1% | 0% | 14 |
| 9 | Ergonomics | 142 | 1% | 0% | 12 |
| 10 | Engineering, Industrial | 112 | 2% | 0% | 21 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | INFORMAT SYST TECHNOL ESI | 91877 | 0% | 100% | 3 |
| 2 | SOFTWARE SYST MODELLING GRP | 91877 | 0% | 100% | 3 |
| 3 | CULTURAL INFORMAT | 91871 | 1% | 50% | 6 |
| 4 | HCI DESIGN | 64835 | 1% | 18% | 12 |
| 5 | EMPIRICAL SOFTWARE ENGN GRP | 61251 | 0% | 100% | 2 |
| 6 | STEAM | 61247 | 0% | 50% | 4 |
| 7 | SYST ELECT ENGN DSIE | 61247 | 0% | 50% | 4 |
| 8 | FEW BUSINESS INFORMAT | 40833 | 0% | 67% | 2 |
| 9 | INFORMAT COMMUN SYST SECUR | 37505 | 1% | 18% | 7 |
| 10 | ALARCOS GRP | 36729 | 1% | 10% | 12 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | REQUIREMENTS ENGINEERING | 833956 | 8% | 34% | 80 |
| 2 | INFORMATION AND SOFTWARE TECHNOLOGY | 39108 | 6% | 2% | 56 |
| 3 | INTERNATIONAL JOURNAL OF SOFTWARE ENGINEERING AND KNOWLEDGE ENGINEERING | 28068 | 3% | 3% | 30 |
| 4 | IEEE SECURITY & PRIVACY | 27866 | 2% | 4% | 24 |
| 5 | IEEE SOFTWARE | 26328 | 4% | 2% | 38 |
| 6 | JOURNAL OF SYSTEMS AND SOFTWARE | 19490 | 5% | 1% | 48 |
| 7 | SOFTWARE AND SYSTEMS MODELING | 18645 | 2% | 4% | 15 |
| 8 | JOURNAL OF OBJECT-ORIENTED PROGRAMMING | 13584 | 1% | 3% | 14 |
| 9 | IEEE TRANSACTIONS ON SOFTWARE ENGINEERING | 13090 | 4% | 1% | 35 |
| 10 | AUTOMATED SOFTWARE ENGINEERING | 12630 | 1% | 5% | 8 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | REQUIREMENTS ENGINEERING | 628068 | 9% | 24% | 87 | Search REQUIREMENTS+ENGINEERING | Search REQUIREMENTS+ENGINEERING |
| 2 | USE CASES | 592898 | 5% | 40% | 48 | Search USE+CASES | Search USE+CASES |
| 3 | GOAL MODELING | 476485 | 2% | 68% | 23 | Search GOAL+MODELING | Search GOAL+MODELING |
| 4 | GOAL ORIENTED REQUIREMENTS ENGINEERING | 465830 | 2% | 89% | 17 | Search GOAL+ORIENTED+REQUIREMENTS+ENGINEERING | Search GOAL+ORIENTED+REQUIREMENTS+ENGINEERING |
| 5 | SECURITY REQUIREMENTS | 445896 | 3% | 47% | 31 | Search SECURITY+REQUIREMENTS | Search SECURITY+REQUIREMENTS |
| 6 | PROBLEM FRAMES | 272399 | 1% | 68% | 13 | Search PROBLEM+FRAMES | Search PROBLEM+FRAMES |
| 7 | REQUIREMENTS ELICITATION | 218901 | 2% | 31% | 23 | Search REQUIREMENTS+ELICITATION | Search REQUIREMENTS+ELICITATION |
| 8 | SECURITY REQUIREMENTS ENGINEERING | 217781 | 1% | 89% | 8 | Search SECURITY+REQUIREMENTS+ENGINEERING | Search SECURITY+REQUIREMENTS+ENGINEERING |
| 9 | SECURITY ENGINEERING | 195985 | 2% | 40% | 16 | Search SECURITY+ENGINEERING | Search SECURITY+ENGINEERING |
| 10 | MISUSE CASES | 166737 | 1% | 78% | 7 | Search MISUSE+CASES | Search MISUSE+CASES |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | UZUNOV, AV , FERNANDEZ, EB , FALKNER, K , (2012) ENGINEERING SECURITY INTO DISTRIBUTED SYSTEMS: A SURVEY OF METHODOLOGIES.JOURNAL OF UNIVERSAL COMPUTER SCIENCE. VOL. 18. ISSUE 20. P. 2920 -3006 | 28 | 61% | 6 |
| 2 | TIWARI, S , GUPTA, A , (2015) A SYSTEMATIC LITERATURE REVIEW OF USE CASE SPECIFICATIONS RESEARCH.INFORMATION AND SOFTWARE TECHNOLOGY. VOL. 67. ISSUE . P. 128 -158 | 27 | 50% | 1 |
| 3 | JIN, Z , LIU, WR , ZOWGHI, D , WEI, B , MU, KD , (2013) MEASURING THE SIGNIFICANCE OF INCONSISTENCY IN THE VIEWPOINTS FRAMEWORK.SCIENCE OF COMPUTER PROGRAMMING. VOL. 78. ISSUE 9. P. 1572 -1599 | 17 | 81% | 2 |
| 4 | YAMAMOTO, S , KAIYA, H , COX, K , BLEISTEIN, S , (2006) GOAL ORIENTED REQUIREMENTS ENGINEERING: TRENDS AND ISSUES.IEICE TRANSACTIONS ON INFORMATION AND SYSTEMS. VOL. E89D. ISSUE 11. P. 2701 -2711 | 17 | 89% | 6 |
| 5 | PAJA, E , DALPIAZ, F , GIORGINI, P , (2015) MODELLING AND REASONING ABOUT SECURITY REQUIREMENTS IN SOCIO-TECHNICAL SYSTEMS.DATA & KNOWLEDGE ENGINEERING. VOL. 98. ISSUE . P. 123 -143 | 12 | 92% | 4 |
| 6 | SCANDARIATO, R , WUYTS, K , JOOSEN, W , (2015) A DESCRIPTIVE STUDY OF MICROSOFT'S THREAT MODELING TECHNIQUE.REQUIREMENTS ENGINEERING. VOL. 20. ISSUE 2. P. 163 -180 | 12 | 92% | 3 |
| 7 | MU, KD , WANG, KW , WEN, L , (2014) APPROACHES TO MEASURING INCONSISTENCY FOR STRATIFIED KNOWLEDGE BASES.INTERNATIONAL JOURNAL OF APPROXIMATE REASONING. VOL. 55. ISSUE 2. P. 529-556 | 14 | 82% | 2 |
| 8 | HOUMB, SH , ISLAM, S , KNAUSS, E , JURJENS, J , SCHNEIDER, K , (2010) ELICITING SECURITY REQUIREMENTS AND TRACING THEM TO DESIGN: AN INTEGRATION OF COMMON CRITERIA, HEURISTICS, AND UMLSEC.REQUIREMENTS ENGINEERING. VOL. 15. ISSUE 1. P. 63 -93 | 12 | 100% | 23 |
| 9 | SOUAG, A , MAZO, R , SALINESI, C , COMYN-WATTIAU, I , (2016) REUSABLE KNOWLEDGE IN SECURITY REQUIREMENTS ENGINEERING: A SYSTEMATIC MAPPING STUDY.REQUIREMENTS ENGINEERING. VOL. 21. ISSUE 2. P. 251 -283 | 14 | 74% | 1 |
| 10 | MU, KD , HONG, J , JIN, Z , LIU, WR , (2013) FROM INCONSISTENCY HANDLING TO NON-CANONICAL REQUIREMENTS MANAGEMENT: A LOGICAL PERSPECTIVE.INTERNATIONAL JOURNAL OF APPROXIMATE REASONING. VOL. 54. ISSUE 1. P. 109 -131 | 14 | 82% | 2 |
Classes with closest relation at Level 1 |