Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
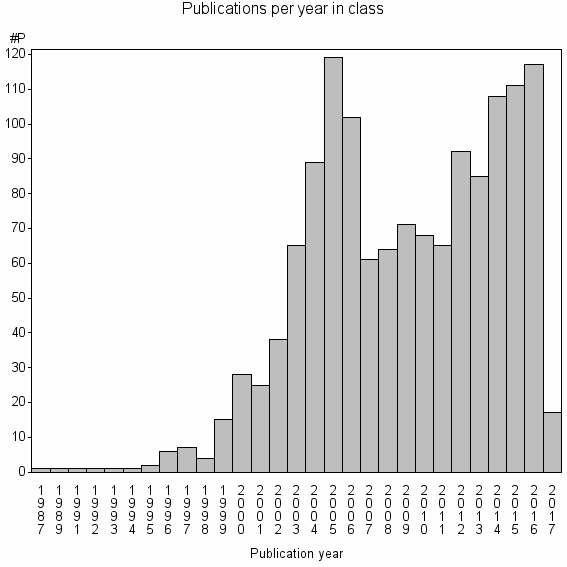
| 7457 | 1365 | 29.4 | 29% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | INTRUSION DETECTION | authKW | 3359554 | 24% | 46% | 330 |
| 2 | INTRUSION DETECTION SYSTEM | authKW | 1275305 | 8% | 51% | 112 |
| 3 | ALERT CORRELATION | authKW | 685029 | 3% | 88% | 35 |
| 4 | ANOMALY DETECTION | authKW | 656682 | 12% | 17% | 170 |
| 5 | MASQUERADE DETECTION | authKW | 335529 | 1% | 100% | 15 |
| 6 | MISUSE DETECTION | authKW | 308520 | 1% | 69% | 20 |
| 7 | NETWORK INTRUSION DETECTION | authKW | 287461 | 2% | 46% | 28 |
| 8 | NETWORK SECURITY | authKW | 282126 | 8% | 12% | 104 |
| 9 | SYSTEM CALL | authKW | 207033 | 1% | 49% | 19 |
| 10 | COMPUTER SECURITY | authKW | 189522 | 4% | 16% | 54 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 35041 | 42% | 0% | 567 |
| 2 | Computer Science, Theory & Methods | 13962 | 28% | 0% | 383 |
| 3 | Computer Science, Artificial Intelligence | 12854 | 26% | 0% | 349 |
| 4 | Telecommunications | 10302 | 23% | 0% | 318 |
| 5 | Computer Science, Hardware & Architecture | 8763 | 14% | 0% | 197 |
| 6 | Computer Science, Software Engineering | 7323 | 17% | 0% | 235 |
| 7 | Engineering, Electrical & Electronic | 2023 | 24% | 0% | 330 |
| 8 | Computer Science, Interdisciplinary Applications | 1036 | 8% | 0% | 109 |
| 9 | Operations Research & Management Science | 340 | 4% | 0% | 55 |
| 10 | Engineering, General | 105 | 3% | 0% | 36 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | SECUR GRP SECREG | 89474 | 0% | 100% | 4 |
| 2 | RELIABLE SOFTWARE GRP | 67100 | 0% | 50% | 6 |
| 3 | INFORMAT SYST ASSURANCE | 62130 | 0% | 56% | 5 |
| 4 | CNSIS | 44737 | 0% | 100% | 2 |
| 5 | NAI S | 44737 | 0% | 100% | 2 |
| 6 | NETWORKED SYST INFORMAT SECUR | 44737 | 0% | 100% | 2 |
| 7 | INFORMAT SECUR EXCELLENCE | 40261 | 0% | 60% | 3 |
| 8 | COMMUN DECOM | 33550 | 0% | 50% | 3 |
| 9 | GRP SIGNALS TELEMAT COMMUN | 29823 | 0% | 67% | 2 |
| 10 | IIRTRC ELECT ENGN COMP SCI | 29823 | 0% | 67% | 2 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 113928 | 6% | 7% | 78 |
| 2 | SECURITY AND COMMUNICATION NETWORKS | 41940 | 4% | 4% | 51 |
| 3 | JOURNAL OF NETWORK AND COMPUTER APPLICATIONS | 20876 | 3% | 2% | 40 |
| 4 | LECTURE NOTES IN COMPUTER SCIENCE | 13515 | 17% | 0% | 233 |
| 5 | IEEE SECURITY & PRIVACY | 12740 | 1% | 3% | 19 |
| 6 | COMPUTER NETWORKS | 11551 | 3% | 1% | 44 |
| 7 | INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT | 9340 | 1% | 4% | 10 |
| 8 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 7775 | 1% | 3% | 10 |
| 9 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 6673 | 1% | 2% | 12 |
| 10 | COMPUTER COMMUNICATIONS | 6133 | 3% | 1% | 35 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | INTRUSION DETECTION | 3359554 | 24% | 46% | 330 | Search INTRUSION+DETECTION | Search INTRUSION+DETECTION |
| 2 | INTRUSION DETECTION SYSTEM | 1275305 | 8% | 51% | 112 | Search INTRUSION+DETECTION+SYSTEM | Search INTRUSION+DETECTION+SYSTEM |
| 3 | ALERT CORRELATION | 685029 | 3% | 88% | 35 | Search ALERT+CORRELATION | Search ALERT+CORRELATION |
| 4 | ANOMALY DETECTION | 656682 | 12% | 17% | 170 | Search ANOMALY+DETECTION | Search ANOMALY+DETECTION |
| 5 | MASQUERADE DETECTION | 335529 | 1% | 100% | 15 | Search MASQUERADE+DETECTION | Search MASQUERADE+DETECTION |
| 6 | MISUSE DETECTION | 308520 | 1% | 69% | 20 | Search MISUSE+DETECTION | Search MISUSE+DETECTION |
| 7 | NETWORK INTRUSION DETECTION | 287461 | 2% | 46% | 28 | Search NETWORK+INTRUSION+DETECTION | Search NETWORK+INTRUSION+DETECTION |
| 8 | NETWORK SECURITY | 282126 | 8% | 12% | 104 | Search NETWORK+SECURITY | Search NETWORK+SECURITY |
| 9 | SYSTEM CALL | 207033 | 1% | 49% | 19 | Search SYSTEM+CALL | Search SYSTEM+CALL |
| 10 | COMPUTER SECURITY | 189522 | 4% | 16% | 54 | Search COMPUTER+SECURITY | Search COMPUTER+SECURITY |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | BHUYAN, MH , BHATTACHARYYA, DK , KALITA, JK , (2014) NETWORK ANOMALY DETECTION: METHODS, SYSTEMS AND TOOLS.IEEE COMMUNICATIONS SURVEYS AND TUTORIALS. VOL. 16. ISSUE 1. P. 303 -336 | 46 | 59% | 47 |
| 2 | LIN, WC , KE, SW , TSAI, CF , (2015) CANN: AN INTRUSION DETECTION SYSTEM BASED ON COMBINING CLUSTER CENTERS AND NEAREST NEIGHBORS.KNOWLEDGE-BASED SYSTEMS. VOL. 78. ISSUE . P. 13 -21 | 29 | 88% | 18 |
| 3 | TSAI, CF , HSU, YF , LIN, CY , LIN, WY , (2009) INTRUSION DETECTION BY MACHINE LEARNING: A REVIEW.EXPERT SYSTEMS WITH APPLICATIONS. VOL. 36. ISSUE 10. P. 11994 -12000 | 25 | 83% | 130 |
| 4 | HUBBALLI, N , SURYANARAYANAN, V , (2014) FALSE ALARM MINIMIZATION TECHNIQUES IN SIGNATURE-BASED INTRUSION DETECTION SYSTEMS: A SURVEY.COMPUTER COMMUNICATIONS. VOL. 49. ISSUE . P. 1 -17 | 25 | 81% | 8 |
| 5 | WU, SX , BANZHAF, W , (2010) THE USE OF COMPUTATIONAL INTELLIGENCE IN INTRUSION DETECTION SYSTEMS: A REVIEW.APPLIED SOFT COMPUTING. VOL. 10. ISSUE 1. P. 1 -35 | 37 | 44% | 134 |
| 6 | CHEN, CM , CHEN, YL , LIN, HC , (2010) AN EFFICIENT NETWORK INTRUSION DETECTION.COMPUTER COMMUNICATIONS. VOL. 33. ISSUE 4. P. 477 -484 | 23 | 92% | 12 |
| 7 | KHOR, KC , TING, CY , PHON-AMNUAISUK, S , (2012) A CASCADED CLASSIFIER APPROACH FOR IMPROVING DETECTION RATES ON RARE ATTACK CATEGORIES IN NETWORK INTRUSION DETECTION.APPLIED INTELLIGENCE. VOL. 36. ISSUE 2. P. 320-329 | 20 | 91% | 25 |
| 8 | AHMED, M , MAHMOOD, AN , HU, JK , (2016) A SURVEY OF NETWORK ANOMALY DETECTION TECHNIQUES.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 60. ISSUE . P. 19 -31 | 21 | 68% | 4 |
| 9 | PATEL, A , TAGHAVI, M , BAKHTIYARI, K , CELESTINO, J , (2013) AN INTRUSION DETECTION AND PREVENTION SYSTEM IN CLOUD COMPUTING: A SYSTEMATIC REVIEW.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 36. ISSUE 1. P. 25-41 | 22 | 67% | 53 |
| 10 | ELSHOUSH, HT , OSMAN, IM , (2011) ALERT CORRELATION IN COLLABORATIVE INTELLIGENT INTRUSION DETECTION SYSTEMS-A SURVEY.APPLIED SOFT COMPUTING. VOL. 11. ISSUE 7. P. 4349-4365 | 18 | 95% | 27 |
Classes with closest relation at Level 1 |