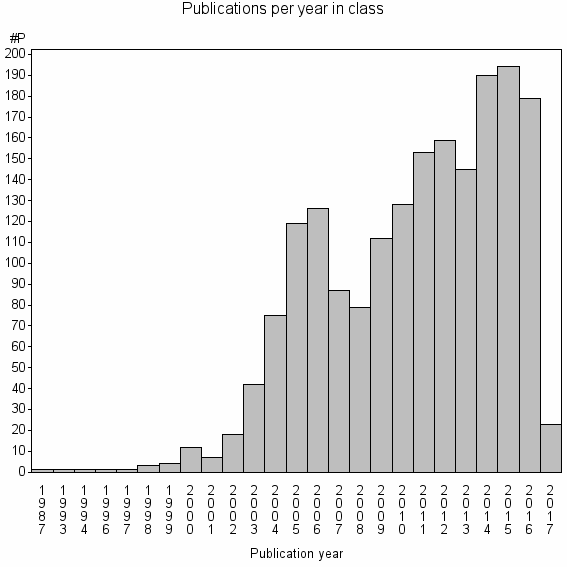
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 4035 | 1860 | 29.7 | 30% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | TRUST MANAGEMENT | authKW | 816747 | 5% | 51% | 98 |
| 2 | TRUST MODEL | authKW | 662025 | 4% | 61% | 66 |
| 3 | REPUTATION SYSTEM | authKW | 466918 | 2% | 66% | 43 |
| 4 | WORMHOLE ATTACK | authKW | 366841 | 2% | 72% | 31 |
| 5 | MOBILE AD HOC NETWORKS | authKW | 307690 | 7% | 14% | 133 |
| 6 | REPUTATION | authKW | 285379 | 8% | 12% | 146 |
| 7 | REPUTATION SYSTEMS | authKW | 271700 | 2% | 47% | 35 |
| 8 | SECURE ROUTING | authKW | 270816 | 2% | 50% | 33 |
| 9 | TRUST EVALUATION | authKW | 230101 | 1% | 52% | 27 |
| 10 | MANET | authKW | 195665 | 5% | 13% | 89 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 57822 | 46% | 0% | 849 |
| 2 | Telecommunications | 43358 | 40% | 0% | 752 |
| 3 | Computer Science, Hardware & Architecture | 14378 | 16% | 0% | 294 |
| 4 | Computer Science, Theory & Methods | 14347 | 24% | 0% | 455 |
| 5 | Computer Science, Software Engineering | 6177 | 14% | 0% | 254 |
| 6 | Computer Science, Artificial Intelligence | 5719 | 15% | 0% | 277 |
| 7 | Engineering, Electrical & Electronic | 3366 | 26% | 0% | 491 |
| 8 | Computer Science, Interdisciplinary Applications | 555 | 5% | 0% | 98 |
| 9 | Automation & Control Systems | 134 | 2% | 0% | 40 |
| 10 | Operations Research & Management Science | 95 | 2% | 0% | 39 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ALGORITHMS SECUR GRP | 52527 | 0% | 80% | 4 |
| 2 | EMEDIA | 37517 | 0% | 57% | 4 |
| 3 | INGN INFORMAC COMUNICAC | 37501 | 1% | 19% | 12 |
| 4 | DCSL | 36932 | 0% | 75% | 3 |
| 5 | BUSINESS INFORMAT TECHNOL MEDIA | 32830 | 0% | 100% | 2 |
| 6 | EXTENDED ENTERPRISE BUSINESS INTELLIGENCE | 32830 | 0% | 100% | 2 |
| 7 | GRP IND UNIV COOPERAT | 32830 | 0% | 100% | 2 |
| 8 | INFORMAT TECHNOL COMMUN SECUR | 32830 | 0% | 100% | 2 |
| 9 | MULTIMEDIA NETWORKS CEMNET | 32830 | 0% | 100% | 2 |
| 10 | YD | 32830 | 0% | 100% | 2 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | SECURITY AND COMMUNICATION NETWORKS | 61349 | 4% | 5% | 72 |
| 2 | PEER-TO-PEER NETWORKING AND APPLICATIONS | 34546 | 2% | 7% | 29 |
| 3 | AD HOC NETWORKS | 22594 | 2% | 3% | 42 |
| 4 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 21282 | 1% | 5% | 25 |
| 5 | IEEE TRANSACTIONS ON MOBILE COMPUTING | 12302 | 2% | 2% | 37 |
| 6 | COMPUTATIONAL INTELLIGENCE | 11381 | 1% | 4% | 19 |
| 7 | COMPUTER NETWORKS | 10495 | 3% | 1% | 49 |
| 8 | JOURNAL OF NETWORK AND COMPUTER APPLICATIONS | 10401 | 2% | 2% | 33 |
| 9 | COMPUTERS & SECURITY | 9978 | 1% | 2% | 27 |
| 10 | ELECTRONIC COMMERCE RESEARCH | 7289 | 0% | 5% | 9 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | TRUST MANAGEMENT | 816747 | 5% | 51% | 98 | Search TRUST+MANAGEMENT | Search TRUST+MANAGEMENT |
| 2 | TRUST MODEL | 662025 | 4% | 61% | 66 | Search TRUST+MODEL | Search TRUST+MODEL |
| 3 | REPUTATION SYSTEM | 466918 | 2% | 66% | 43 | Search REPUTATION+SYSTEM | Search REPUTATION+SYSTEM |
| 4 | WORMHOLE ATTACK | 366841 | 2% | 72% | 31 | Search WORMHOLE+ATTACK | Search WORMHOLE+ATTACK |
| 5 | MOBILE AD HOC NETWORKS | 307690 | 7% | 14% | 133 | Search MOBILE+AD+HOC+NETWORKS | Search MOBILE+AD+HOC+NETWORKS |
| 6 | REPUTATION | 285379 | 8% | 12% | 146 | Search REPUTATION | Search REPUTATION |
| 7 | REPUTATION SYSTEMS | 271700 | 2% | 47% | 35 | Search REPUTATION+SYSTEMS | Search REPUTATION+SYSTEMS |
| 8 | SECURE ROUTING | 270816 | 2% | 50% | 33 | Search SECURE+ROUTING | Search SECURE+ROUTING |
| 9 | TRUST EVALUATION | 230101 | 1% | 52% | 27 | Search TRUST+EVALUATION | Search TRUST+EVALUATION |
| 10 | MANET | 195665 | 5% | 13% | 89 | Search MANET | Search MANET |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | KUMAR, S , DUTTA, K , (2016) INTRUSION DETECTION IN MOBILE AD HOC NETWORKS: TECHNIQUES, SYSTEMS, AND FUTURE CHALLENGES.SECURITY AND COMMUNICATION NETWORKS. VOL. 9. ISSUE 14. P. 2484 -2556 | 57 | 59% | 0 |
| 2 | RUAN, YF , DURRESI, A , (2016) A SURVEY OF TRUST MANAGEMENT SYSTEMS FOR ONLINE SOCIAL COMMUNITIES - TRUST MODELING, TRUST INFERENCE AND ATTACKS.KNOWLEDGE-BASED SYSTEMS. VOL. 106. ISSUE . P. 150 -163 | 35 | 71% | 0 |
| 3 | BIDGOLY, AJ , LADANI, BT , (2016) BENCHMARKING REPUTATION SYSTEMS: A QUANTITATIVE VERIFICATION APPROACH.COMPUTERS IN HUMAN BEHAVIOR. VOL. 57. ISSUE . P. 274 -291 | 23 | 88% | 2 |
| 4 | BIDGOLY, AJ , LADANI, BT , (2016) MODELING AND QUANTITATIVE VERIFICATION OF TRUST SYSTEMS AGAINST MALICIOUS ATTACKERS.COMPUTER JOURNAL. VOL. 59. ISSUE 7. P. 1005 -1027 | 24 | 96% | 0 |
| 5 | JIANG, WJ , WANG, GJ , BHUIYAN, MZA , WU, J , (2016) UNDERSTANDING GRAPH-BASED TRUST EVALUATION IN ONLINE SOCIAL NETWORKS: METHODOLOGIES AND CHALLENGES.ACM COMPUTING SURVEYS. VOL. 49. ISSUE 1. P. - | 31 | 70% | 0 |
| 6 | KRAOUNAKIS, S , DEMETROPOULOS, IN , MICHALAS, A , OBAIDAT, MS , SARIGIANNIDIS, PG , LOUTA, MD , (2015) A ROBUST REPUTATION-BASED COMPUTATIONAL MODEL FOR TRUST ESTABLISHMENT IN PERVASIVE SYSTEMS.IEEE SYSTEMS JOURNAL. VOL. 9. ISSUE 3. P. 878 -891 | 25 | 86% | 1 |
| 7 | BIDGOLY, AJ , LADANI, BT , (2015) MODELLING AND QUANTITATIVE VERIFICATION OF REPUTATION SYSTEMS AGAINST MALICIOUS ATTACKERS.COMPUTER JOURNAL. VOL. 58. ISSUE 10. P. 2567 -2582 | 19 | 90% | 0 |
| 8 | VAVILIS, S , PETKOVIC, M , ZANNONE, N , (2014) A REFERENCE MODEL FOR REPUTATION SYSTEMS.DECISION SUPPORT SYSTEMS. VOL. 61. ISSUE . P. 147 -154 | 19 | 79% | 15 |
| 9 | AHMED, A , ABU BAKAR, K , CHANNA, MI , HASEEB, K , KHAN, AW , (2015) A SURVEY ON TRUST BASED DETECTION AND ISOLATION OF MALICIOUS NODES IN AD-HOC AND SENSOR NETWORKS.FRONTIERS OF COMPUTER SCIENCE. VOL. 9. ISSUE 2. P. 280 -296 | 18 | 86% | 4 |
| 10 | FAN, XX , LI, MC , MA, JH , REN, YZ , ZHAO, H , SU, ZY , (2012) BEHAVIOR-BASED REPUTATION MANAGEMENT IN P2P FILE-SHARING NETWORKS.JOURNAL OF COMPUTER AND SYSTEM SCIENCES. VOL. 78. ISSUE 6. P. 1737 -1750 | 19 | 86% | 9 |
Classes with closest relation at Level 1 |