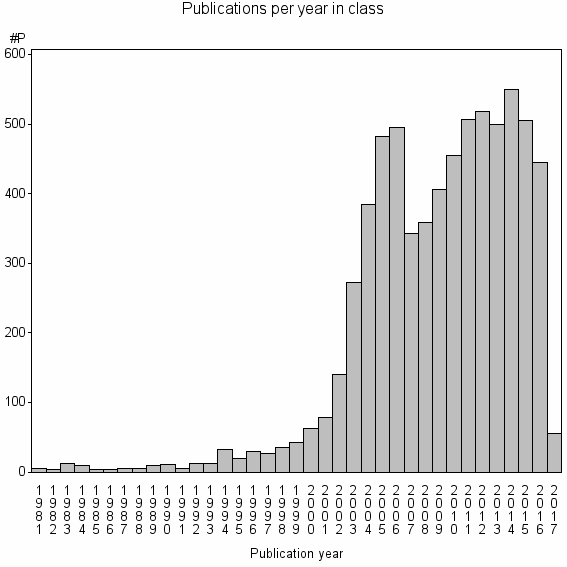
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 1665 | 6842 | 27.3 | 27% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | PEER TO PEER | authKW | 1112049 | 7% | 51% | 487 |
| 2 | PEER TO PEER NETWORKS | authKW | 541068 | 3% | 60% | 201 |
| 3 | PEER-TO-PEER NETWORKING AND APPLICATIONS | journal | 390770 | 3% | 47% | 187 |
| 4 | P2P | authKW | 382393 | 3% | 47% | 181 |
| 5 | TRUST MANAGEMENT | authKW | 327226 | 2% | 62% | 119 |
| 6 | BITTORRENT | authKW | 321198 | 1% | 81% | 89 |
| 7 | ACCESS CONTROL | authKW | 318304 | 4% | 27% | 265 |
| 8 | DISTRIBUTED HASH TABLE | authKW | 297624 | 1% | 69% | 97 |
| 9 | PEER TO PEER SYSTEMS | authKW | 243524 | 1% | 59% | 92 |
| 10 | OVERLAY NETWORKS | authKW | 228994 | 2% | 40% | 130 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 197762 | 44% | 2% | 3013 |
| 2 | Computer Science, Theory & Methods | 111776 | 35% | 1% | 2413 |
| 3 | Telecommunications | 100461 | 32% | 1% | 2205 |
| 4 | Computer Science, Hardware & Architecture | 54754 | 16% | 1% | 1100 |
| 5 | Computer Science, Software Engineering | 45685 | 19% | 1% | 1310 |
| 6 | Engineering, Electrical & Electronic | 12333 | 26% | 0% | 1803 |
| 7 | Computer Science, Artificial Intelligence | 9485 | 10% | 0% | 699 |
| 8 | Computer Science, Interdisciplinary Applications | 1215 | 4% | 0% | 289 |
| 9 | Operations Research & Management Science | 173 | 2% | 0% | 111 |
| 10 | Logic | 157 | 0% | 0% | 26 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMP SCI | 60519 | 21% | 1% | 1449 |
| 2 | COMP SCI ENGN | 30866 | 7% | 1% | 500 |
| 3 | CERIAS | 28126 | 0% | 25% | 25 |
| 4 | CENT PLAINS ECON ZONE WISDOM TOURISM COOPERAT INN | 22305 | 0% | 100% | 5 |
| 5 | COMP SCI TECHNOL | 20572 | 4% | 2% | 267 |
| 6 | DISTRIBUTED OBJECT PROGRAMMING | 18586 | 0% | 83% | 5 |
| 7 | DATABASES DISTRIBUTED SYST GRP | 17840 | 0% | 67% | 6 |
| 8 | COMP ENGN | 17713 | 4% | 1% | 275 |
| 9 | TRUSTED SYST | 16055 | 0% | 60% | 6 |
| 10 | EMEDIA | 15929 | 0% | 71% | 5 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | PEER-TO-PEER NETWORKING AND APPLICATIONS | 390770 | 3% | 47% | 187 |
| 2 | COMPUTER NETWORKS | 61351 | 3% | 6% | 227 |
| 3 | LECTURE NOTES IN COMPUTER SCIENCE | 53702 | 15% | 1% | 1042 |
| 4 | IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS | 52172 | 3% | 6% | 205 |
| 5 | COMPUTERS & SECURITY | 37210 | 1% | 8% | 100 |
| 6 | SECURITY AND COMMUNICATION NETWORKS | 32047 | 1% | 7% | 100 |
| 7 | FUTURE GENERATION COMPUTER SYSTEMS-THE INTERNATIONAL JOURNAL OF ESCIENCE | 30800 | 2% | 6% | 121 |
| 8 | IEEE INTERNET COMPUTING | 30422 | 1% | 9% | 80 |
| 9 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 28857 | 1% | 19% | 35 |
| 10 | JOURNAL OF NETWORK AND COMPUTER APPLICATIONS | 24900 | 1% | 6% | 98 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | PEER TO PEER | 1112049 | 7% | 51% | 487 | Search PEER+TO+PEER | Search PEER+TO+PEER |
| 2 | PEER TO PEER NETWORKS | 541068 | 3% | 60% | 201 | Search PEER+TO+PEER+NETWORKS | Search PEER+TO+PEER+NETWORKS |
| 3 | P2P | 382393 | 3% | 47% | 181 | Search P2P | Search P2P |
| 4 | TRUST MANAGEMENT | 327226 | 2% | 62% | 119 | Search TRUST+MANAGEMENT | Search TRUST+MANAGEMENT |
| 5 | BITTORRENT | 321198 | 1% | 81% | 89 | Search BITTORRENT | Search BITTORRENT |
| 6 | ACCESS CONTROL | 318304 | 4% | 27% | 265 | Search ACCESS+CONTROL | Search ACCESS+CONTROL |
| 7 | DISTRIBUTED HASH TABLE | 297624 | 1% | 69% | 97 | Search DISTRIBUTED+HASH+TABLE | Search DISTRIBUTED+HASH+TABLE |
| 8 | PEER TO PEER SYSTEMS | 243524 | 1% | 59% | 92 | Search PEER+TO+PEER+SYSTEMS | Search PEER+TO+PEER+SYSTEMS |
| 9 | OVERLAY NETWORKS | 228994 | 2% | 40% | 130 | Search OVERLAY+NETWORKS | Search OVERLAY+NETWORKS |
| 10 | P2P NETWORKS | 208173 | 1% | 66% | 71 | Search P2P+NETWORKS | Search P2P+NETWORKS |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | MALATRAS, A , (2015) STATE-OF-THE-ART SURVEY ON P2P OVERLAY NETWORKS IN PERVASIVE COMPUTING ENVIRONMENTS.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 55. ISSUE . P. 1 -23 | 52 | 72% | 8 |
| 2 | KUMAR, S , DUTTA, K , (2016) INTRUSION DETECTION IN MOBILE AD HOC NETWORKS: TECHNIQUES, SYSTEMS, AND FUTURE CHALLENGES.SECURITY AND COMMUNICATION NETWORKS. VOL. 9. ISSUE 14. P. 2484 -2556 | 57 | 59% | 0 |
| 3 | KORZUN, D , GURTOV, A , (2011) SURVEY ON HIERARCHICAL ROUTING SCHEMES IN "FLAT" DISTRIBUTED HASH TABLES.PEER-TO-PEER NETWORKING AND APPLICATIONS. VOL. 4. ISSUE 4. P. 346 -375 | 40 | 93% | 3 |
| 4 | KORZUN, D , GURTOV, A , (2014) HIERARCHICAL ARCHITECTURES IN STRUCTURED PEER-TO-PEER OVERLAY NETWORKS.PEER-TO-PEER NETWORKING AND APPLICATIONS. VOL. 7. ISSUE 4. P. 359 -395 | 39 | 87% | 2 |
| 5 | LIN, CH , ZSENG, JJ , HSIEH, SY , (2015) IMPROVING THE SEARCH MECHANISM FOR UNSTRUCTURED PEER-TO-PEER NETWORKS USING THE STATISTICAL MATRIX FORM.IEEE ACCESS. VOL. 3. ISSUE . P. 926 -941 | 37 | 82% | 1 |
| 6 | RUAN, YF , DURRESI, A , (2016) A SURVEY OF TRUST MANAGEMENT SYSTEMS FOR ONLINE SOCIAL COMMUNITIES - TRUST MODELING, TRUST INFERENCE AND ATTACKS.KNOWLEDGE-BASED SYSTEMS. VOL. 106. ISSUE . P. 150 -163 | 35 | 71% | 0 |
| 7 | BIDGOLY, AJ , LADANI, BT , (2016) BENCHMARKING REPUTATION SYSTEMS: A QUANTITATIVE VERIFICATION APPROACH.COMPUTERS IN HUMAN BEHAVIOR. VOL. 57. ISSUE . P. 274 -291 | 23 | 88% | 2 |
| 8 | KOSKELA, T , KASSINEN, O , HARJULA, E , YLIANTTILA, M , (2013) P2P GROUP MANAGEMENT SYSTEMS: A CONCEPTUAL ANALYSIS.ACM COMPUTING SURVEYS. VOL. 45. ISSUE 2. P. - | 26 | 96% | 0 |
| 9 | BIDGOLY, AJ , LADANI, BT , (2016) MODELING AND QUANTITATIVE VERIFICATION OF TRUST SYSTEMS AGAINST MALICIOUS ATTACKERS.COMPUTER JOURNAL. VOL. 59. ISSUE 7. P. 1005 -1027 | 24 | 96% | 0 |
| 10 | SANCHEZ-ARTIGAS, M , HERRERA, B , (2013) UNDERSTANDING THE EFFECTS OF P2P DYNAMICS ON TRUST BOOTSTRAPPING.INFORMATION SCIENCES. VOL. 236. ISSUE . P. 33 -55 | 24 | 96% | 3 |
Classes with closest relation at Level 2 |