Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
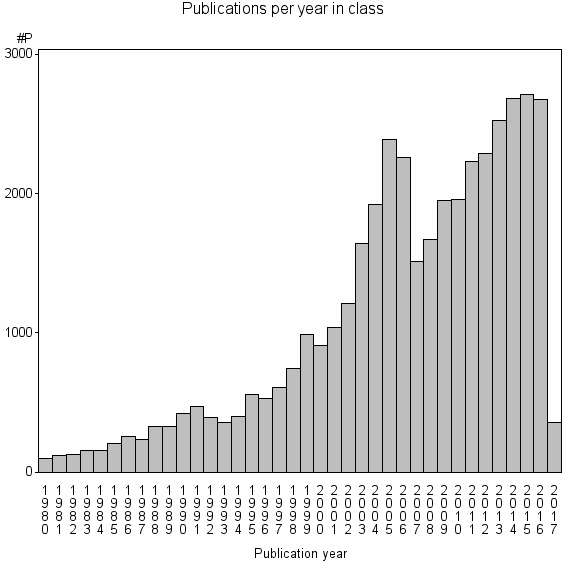
| 295 | 41419 | 21.3 | 40% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | CRYPTOGRAPHY | authKW | 869180 | 4% | 69% | 1706 |
| 2 | COMPUTER SCIENCE, THEORY & METHODS | WoSSC | 487779 | 30% | 6% | 12448 |
| 3 | IEEE TRANSACTIONS ON INFORMATION THEORY | journal | 482644 | 6% | 27% | 2479 |
| 4 | COMPUTER SCIENCE, INFORMATION SYSTEMS | WoSSC | 452131 | 27% | 6% | 11313 |
| 5 | DESIGNS CODES AND CRYPTOGRAPHY | journal | 391600 | 2% | 56% | 959 |
| 6 | AUTHENTICATION | authKW | 366096 | 3% | 46% | 1097 |
| 7 | FINITE FIELDS | authKW | 316778 | 2% | 56% | 766 |
| 8 | FINITE FIELDS AND THEIR APPLICATIONS | journal | 304079 | 2% | 64% | 650 |
| 9 | NETWORK CODING | authKW | 294900 | 2% | 58% | 693 |
| 10 | RFID | authKW | 292655 | 2% | 48% | 838 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Theory & Methods | 487779 | 30% | 6% | 12448 |
| 2 | Computer Science, Information Systems | 452131 | 27% | 6% | 11313 |
| 3 | Telecommunications | 181778 | 18% | 4% | 7425 |
| 4 | Computer Science, Hardware & Architecture | 170624 | 12% | 5% | 4814 |
| 5 | Engineering, Electrical & Electronic | 113343 | 32% | 1% | 13158 |
| 6 | Mathematics, Applied | 67321 | 17% | 2% | 7024 |
| 7 | Computer Science, Software Engineering | 54085 | 9% | 2% | 3627 |
| 8 | Mathematics | 26684 | 12% | 1% | 5102 |
| 9 | Computer Science, Interdisciplinary Applications | 4558 | 3% | 1% | 1439 |
| 10 | Computer Science, Artificial Intelligence | 3650 | 3% | 1% | 1271 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | STATE INFORMAT SECUR | 245939 | 1% | 57% | 587 |
| 2 | INFORMAT SECUR | 123144 | 1% | 37% | 459 |
| 3 | INFORMAT SECUR GRP | 96160 | 0% | 72% | 182 |
| 4 | CIST | 74405 | 0% | 66% | 153 |
| 5 | COMP SCI | 73514 | 10% | 3% | 4040 |
| 6 | COMP SCI ENGN | 62603 | 4% | 5% | 1772 |
| 7 | COSIC | 51495 | 0% | 81% | 87 |
| 8 | COMP NETWORKS INFORMAT SECUR | 50548 | 0% | 75% | 92 |
| 9 | COMP INFORMAT SECUR | 47362 | 0% | 69% | 94 |
| 10 | COMP SCI INFORMAT ENGN | 47180 | 2% | 8% | 846 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | IEEE TRANSACTIONS ON INFORMATION THEORY | 482644 | 6% | 27% | 2479 |
| 2 | DESIGNS CODES AND CRYPTOGRAPHY | 391600 | 2% | 56% | 959 |
| 3 | FINITE FIELDS AND THEIR APPLICATIONS | 304079 | 2% | 64% | 650 |
| 4 | LECTURE NOTES IN COMPUTER SCIENCE | 290374 | 14% | 7% | 5968 |
| 5 | JOURNAL OF CRYPTOLOGY | 257275 | 1% | 89% | 392 |
| 6 | IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES | 208480 | 4% | 19% | 1507 |
| 7 | SECURITY AND COMMUNICATION NETWORKS | 161797 | 1% | 40% | 553 |
| 8 | ADVANCES IN MATHEMATICS OF COMMUNICATIONS | 129805 | 1% | 70% | 254 |
| 9 | JOURNAL OF SYMBOLIC COMPUTATION | 122994 | 1% | 27% | 616 |
| 10 | APPLICABLE ALGEBRA IN ENGINEERING COMMUNICATION AND COMPUTING | 114603 | 1% | 51% | 308 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | CRYPTOGRAPHY | 869180 | 4% | 69% | 1706 | Search CRYPTOGRAPHY | Search CRYPTOGRAPHY |
| 2 | AUTHENTICATION | 366096 | 3% | 46% | 1097 | Search AUTHENTICATION | Search AUTHENTICATION |
| 3 | FINITE FIELDS | 316778 | 2% | 56% | 766 | Search FINITE+FIELDS | Search FINITE+FIELDS |
| 4 | NETWORK CODING | 294900 | 2% | 58% | 693 | Search NETWORK+CODING | Search NETWORK+CODING |
| 5 | RFID | 292655 | 2% | 48% | 838 | Search RFID | Search RFID |
| 6 | CRYPTANALYSIS | 283449 | 1% | 68% | 565 | Search CRYPTANALYSIS | Search CRYPTANALYSIS |
| 7 | DIGITAL SIGNATURE | 282202 | 1% | 79% | 488 | Search DIGITAL+SIGNATURE | Search DIGITAL+SIGNATURE |
| 8 | LOW DENSITY PARITY CHECK LDPC CODES | 273814 | 1% | 75% | 499 | Search LOW+DENSITY+PARITY+CHECK+LDPC+CODES | Search LOW+DENSITY+PARITY+CHECK+LDPC+CODES |
| 9 | SMART CARD | 259764 | 1% | 75% | 472 | Search SMART+CARD | Search SMART+CARD |
| 10 | ITERATIVE DECODING | 242292 | 1% | 62% | 530 | Search ITERATIVE+DECODING | Search ITERATIVE+DECODING |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | FARASH, MS , ATTARI, MA , KUMARI, S , (2017) CRYPTANALYSIS AND IMPROVEMENT OF A THREE-PARTY PASSWORD-BASED AUTHENTICATED KEY EXCHANGE PROTOCOL WITH USER ANONYMITY USING EXTENDED CHAOTIC MAPS.INTERNATIONAL JOURNAL OF COMMUNICATION SYSTEMS. VOL. 30. ISSUE 1. P. - | 52 | 98% | 4 |
| 2 | FARASH, MS , (2017) AN IMPROVED PASSWORD-BASED AUTHENTICATION SCHEME FOR SESSION INITIATION PROTOCOL USING SMART CARDS WITHOUT VERIFICATION TABLE.INTERNATIONAL JOURNAL OF COMMUNICATION SYSTEMS. VOL. 30. ISSUE 1. P. - | 30 | 91% | 13 |
| 3 | CARLET, C , MESNAGER, S , (2016) FOUR DECADES OF RESEARCH ON BENT FUNCTIONS.DESIGNS CODES AND CRYPTOGRAPHY. VOL. 78. ISSUE 1. P. 5 -50 | 107 | 95% | 3 |
| 4 | FAN, HN , HASAN, MA , (2015) A SURVEY OF SOME RECENT BIT-PARALLEL GF(2(N)) MULTIPLIERS.FINITE FIELDS AND THEIR APPLICATIONS. VOL. 32. ISSUE . P. 5 -43 | 99 | 98% | 6 |
| 5 | BASSOLI, R , MARQUES, H , RODRIGUEZ, J , SHUM, KW , TAFAZOLLI, R , (2013) NETWORK CODING THEORY: A SURVEY.IEEE COMMUNICATIONS SURVEYS AND TUTORIALS. VOL. 15. ISSUE 4. P. 1950 -1978 | 78 | 92% | 22 |
| 6 | HUFFMAN, WC , (2005) ON THE CLASSIFICATION AND ENUMERATION OF SELF-DUAL CODES.FINITE FIELDS AND THEIR APPLICATIONS. VOL. 11. ISSUE 3. P. 451-490 | 89 | 99% | 74 |
| 7 | WANG, D , WANG, P , (2014) ON THE ANONYMITY OF TWO-FACTOR AUTHENTICATION SCHEMES FOR WIRELESS SENSOR NETWORKS: ATTACKS, PRINCIPLE AND SOLUTIONS.COMPUTER NETWORKS. VOL. 73. ISSUE . P. 41 -57 | 67 | 92% | 24 |
| 8 | POTT, A , (2016) ALMOST PERFECT AND PLANAR FUNCTIONS.DESIGNS CODES AND CRYPTOGRAPHY. VOL. 78. ISSUE 1. P. 141 -195 | 84 | 82% | 0 |
| 9 | ORS, SB , PRENEEL, B , VANDEWALLE, J , BATINA, L , (2003) HARDWARE ARCHITECTURES FOR PUBLIC KEY CRYPTOGRAPHY.INTEGRATION-THE VLSI JOURNAL. VOL. 34. ISSUE 1-2. P. 1 -64 | 97 | 93% | 27 |
| 10 | JIANG, Q , WEI, FS , FU, S , MA, JF , LI, GS , ALELAIWI, A , (2016) ROBUST EXTENDED CHAOTIC MAPS-BASED THREE-FACTOR AUTHENTICATION SCHEME PRESERVING BIOMETRIC TEMPLATE PRIVACY.NONLINEAR DYNAMICS. VOL. 83. ISSUE 4. P. 2085 -2101 | 45 | 94% | 9 |
Classes with closest relation at Level 3 |