The course is centered around a project assignement in which students conduct a threat modeling-based cyber risk assessment and suggest a cyber defesne action plan. The course also includes a number of guest lectures related to cyber threat modeling and security risk assessment.
EP2790 Security Analysis of Large-Scale Computer Systems 7.5 credits
This course will be discontinued.
Decision to discontinue this course:
The course will be discontinued at the end of autumn 2027 according to faculty board decision: HS-2025-2310.
Decision date: 2025-10-07
The course will be given for the last time in autumn 2025. The last opportunity for examination in the course will be given in autumn 2027.
Contact the examiner to be examined during the discontinuation period.
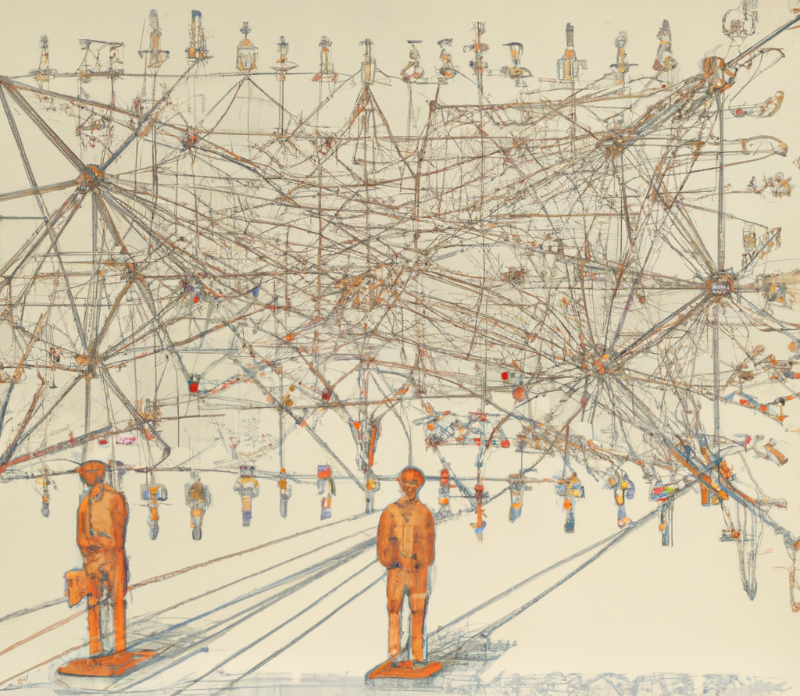
Companies today have thousands of software-based computer systems that all are depending on one another in a large complex network, a system-of-systems. That cyberattacks succeed is to a large extent due to this complexity. The security engineers at a company need to understand the whole system with all its potential vulnerabilities, while an attacker only needs find one way in. Luckily for the defenders, as they have access to the system environment they don't have to start on a blank sheet and discover the environment as the attacker has to do. To add to the complexity, attackers can use a large number of different attack techniques but there also exist plenty of defense mechanisms. Coming up with and maintaining an overall defence solution that at the same time enables the supported business to thrive is a great challenge.
This course teaches a threat modeling-based method for analyzing cybersecurity risks for systems-of-systems. It includes developing and combining models for computer system resilience, threat actor capabilities, and business impacts of realized threats into an overall cyber risk assessment. Moreover the course addresses how cyber risk analysis is used for identifying and arguing for cost efficient defense mechanism selection for protecting the analyzed system-of-systems.
Information per course offering
Course offerings are missing for current or upcoming semesters.
Course syllabus as PDF
Please note: all information from the Course syllabus is available on this page in an accessible format.
Course syllabus EP2790 (Autumn 2025–)Content and learning outcomes
Course disposition
Course contents
This course teaches a threat modeling-based method for analyzing cybersecurity risks for systems-of-systems. It includes developing and combining models for computer system resilience, threat actor capabilities, and business impacts of realized threats into an overall cyber risk assessment. Moreover the course addresses how cyber risk analysis is used for identifying and arguing for cost efficient defense mechanism selection for protecting the analyzed system-of-systems.
Intended learning outcomes
After passing the course, the student should be able to
- model in detail the architectures of large-scale computer systems (including software, networks, etc.)
- carefully and well balanced describe and evaluate threats and attacks in large-scale computer systems
- clearly describe defense mechanisms for computer systems and how these relate to vulnerabilities and attacks
- carry out qualified and well balanced risk analyses based on system models
- in a professional manner report and present models, a cybersecurity risk analysis, and defense strategies for a computer system
in order to
- understand and explain which threats a specific system can have
- understand and explain how attacks work and propagate through a system architecture
- argue why certain risks should be prioritised
- choose an effective defense to decrease risk.
Literature and preparations
Specific prerequisites
Knowledge and skills in programming, 5 credits, equivalent to completed course DD1310-DD1318/DD1331/DD1337/DD100N/ID1018.
Knowledge in cybersecurity, 6 credits, equivalent to completed course DD2391/DD2395/IK2206/IV1013
or
knowledge and skills in ethical hacking, 7,5 credits, equivalent to completed course EN2720
or
knowledge in secure network systems, 7,5 credits, equivalent to completed course EP2500/EP2520.
Literature
Examination and completion
Grading scale
Examination
- PRO1 - Project work, 6.0 credits, grading scale: A, B, C, D, E, FX, F
- SEM1 - Seminars, 1.5 credits, grading scale: P, F
Based on recommendation from KTH’s coordinator for disabilities, the examiner will decide how to adapt an examination for students with documented disability.
The examiner may apply another examination format when re-examining individual students.
If the course is discontinued, students may request to be examined during the following two academic years.
Examiner
Ethical approach
- All members of a group are responsible for the group's work.
- In any assessment, every student shall honestly disclose any help received and sources used.
- In an oral assessment, every student shall be able to present and answer questions about the entire assignment and solution.
Further information
Course room in Canvas
Offered by
Main field of study
Education cycle
Supplementary information
In this course, the EECS code of honor applies, see:
http://www.kth.se/en/eecs/utbildning/hederskodex.
This course overlaps with EP279V.