VIKING
The VIKING project was an EU financed Framework 7 Collaborative STREP Project and was part of themes 4, ICT, and 10, Security. VIKING stands for Vital Infrastructure, Networks, Information and Control Systems Management and was executed between November 1, 2008 and October 31, 2011 by a consortium of industrial and academic partners.
The main objectives of VIKING are:
- To investigate the vulnerability of SCADA systems and the cost of cyber attacks on society
- To propose and test strategies and technologies to mitigate these weaknesses
- To increase the awareness for the importance of critical infrastructures and the need to protect them
Society is increasingly dependent on the proper functioning of the electric power system, which in turn supports most other critical infrastructures: water and sewage systems; telecommunications, internet and computing services; air traffic, railroads and other transportation. Many of these other infrastructures are able to operate without power for shorter periods of time, but larger power outages may be difficult and time consuming to restore. Such outages might thus lead to situations of non-functioning societies with devastating economical and humanitarian consequences. For this reason, this consortium has decided to concentrate its research to the systems for transmission and distribution of electric power. We anticipate that most of the results will be applicable to the protection of other critical infrastructures.
The operation and management of the electric power system depend on computerized industrial control systems. Keeping these systems secure and resilient to external attacks as well as to internal operational errors is thus vital for uninterrupted service. However, this is challenging since the control systems are extremely complex. Yet, the systems are operating under stringent requirements on availability and performance: If control and supervision are not done in real-time, the power network may come to a collapse.
These computerized control system, normally called SCADA standing for System for Control And Data Acquisition, includes functions for remote acquisition of vast amounts of data from measurements placed in strategic points, e.g. power stations, in the geographically widely spread electrical and for the remote control of process devices. Many SCADA systems include computerized models of the process which enables simulation of alternatives process states and of optimization. Due to legal and environmental constraints, e.g. for building of new high voltage power lines or power stations, the primary process itself is difficult to expand which in its turn leads to higher and higher utilization of the existing transmission and generation resources. The process is, in other words, operated closer to its physical limits. Those the SCADA systems are becoming increasingly critical for the operation of the process and therefore are becoming a critical component for the availability and security of the supervised infrastructure.
The objective of the VIKING project is to develop, test and evaluate methodologies for the analysis, design and operation of resilient and secure industrial control systems for critical infrastructures. Methodologies will be developed with a particular focus on increased robustness of the control system. As mentioned, the focus is on power transmission and distribution networks. The project combines a holistic management perspective—in order to counteract sub-optimization in the design—with in-depth analysis and development of security solutions adapted to the specific requirements of networked control systems.
The traditional approach to verify the security of SCADA systems has been ad-hoc testing of existing commercial SCADA system in laboratory environments. The systems to be examined have been installed in different labs and tested by skillful people searching for cyber attacks vulnerabilities. The focus in these tests has been on the protection of the central computer system of the SCADA system, since the central computer system has most connections to the external environment through office networks and Internet.
In the VIKING project we will take an alternative and complementary approach to SCADA system security. Firstly we will study the whole control system from the measurement points in the process itself over the communication network to the central computer system as illustrated in the following picture with the yellow exclamation marks indicating potential targets for cyber attacks.
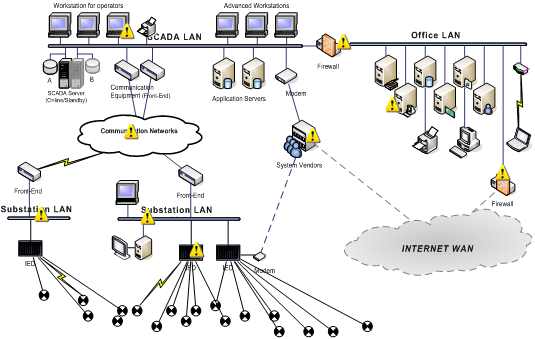
Secondly, and more importantly, we take a model-based approach to investigating SCADA system vulnerability. Models are defined for the SCADA system, for the electrical process as well as of for the society that is dependent on the electricity supply. The society models are used to evaluate the economic consequences coming from disturbances in the electricity supply. The power system models are in turn used to evaluate the effects on the electricity supply by SCADA system misbehavior. Finally, SCADA system models are employed to assess the effect on SCADA system behavior by cyber attacks. Based on analysis performed on these models, VIKING will propose mitigation actions to be taken to decrease or to eliminate these risks. The results of the project will be evaluated on a test-bed that can be configured to simulate the critical infrastructure of a power network and a range of attacks.
The modeling approach is indicated in the following picture.
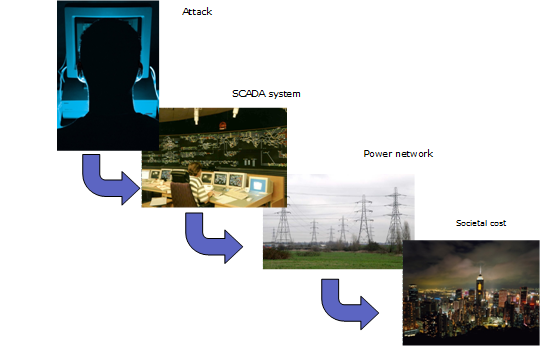
With this approach the project hopes to achieve the following research results.
- Estimates of the security risk and consequences (in terms of monetary loss for the society) based on threats trees, graphical system architecture and society models
- Comparable, quantitative results for IT security for different control system solutions and implementations
- Use of existing model based application as application level Intrusion Detection Systems to detect manipulation of data
- Use of innovative and existing communication solutions to secure power system communication
- Help with identifying ”weak spots” and how to mitigate them
- An environment for performing what-if analyses of the security risk impact of different architecture solutions.
