Research areas
CERCES is organized into four reasearch areas: Embedded Software Platforms, Wireless Communication, Communication and Computation Infrastructures and Resilient Control of Cyber-Physical Systems. Read about them below.
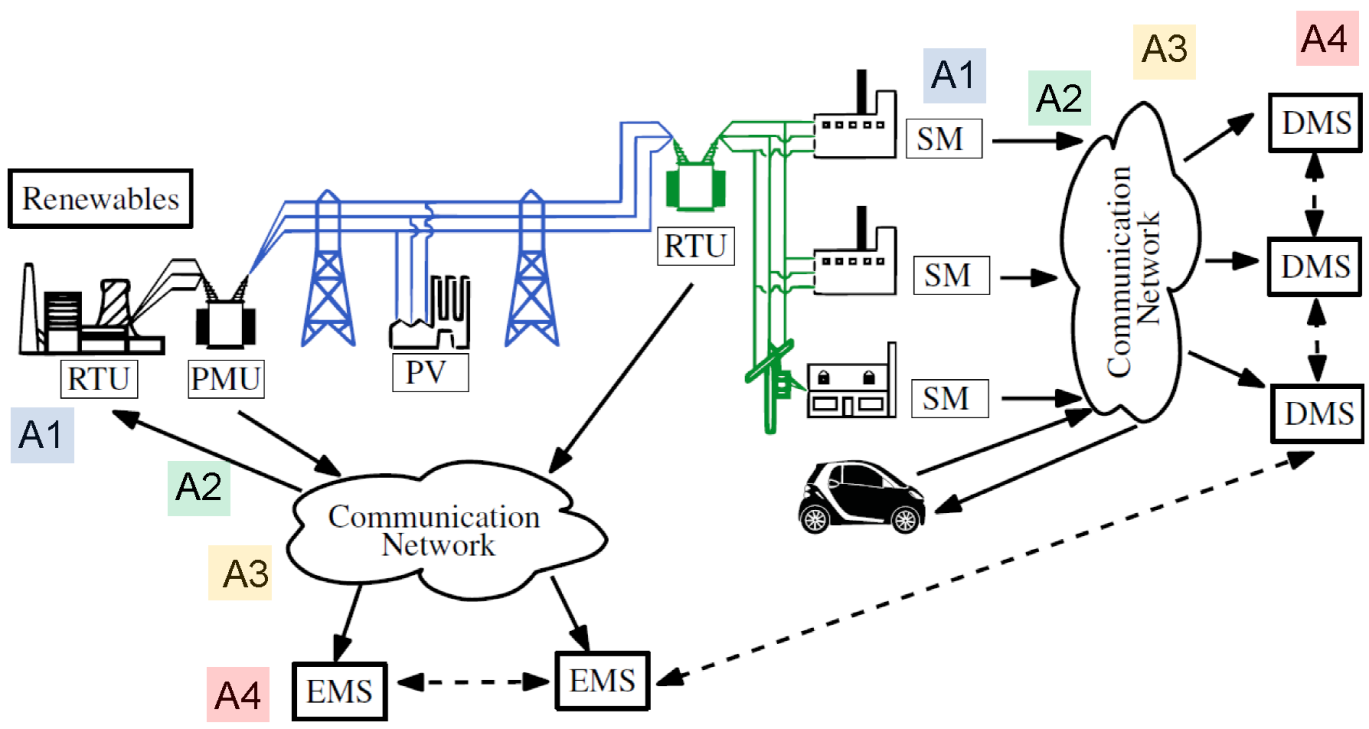
A1: Embedded Software Platforms
Leader: Mads Dam
The first activity concerns the construction of embedded execution platforms for future field devices including PLCs, RTUs, and communication infrastructure equipment such as routers, data diodes, and wireless devices that can meet the very high requirements on security and fault tolerance demanded of future critical infrastructure applications. Virtualization is broadly recognized as a key tool to enable this, since it can be instrumented to provide the required platform integrity and confidentiality properties for highly demanding application domains such as SCADA systems. Moreover, this can be achieved at very high levels of trustworthiness, as we are currently demonstrating in other application areas. Virtualization can be used, even while running unsecure application stacks, to ensure a wealth of desirable properties such as:
- Memory isolation: Provably preventing one application from accessing another application’s working memory.
- Complete mediation: Provably ensuring that all security relevant events of a certain type are checked and processed by a security monitor.
- Code integrity: Provably guaranteeing that only properly authorized code is allowed to execute on a given virtualized processing platform.
By itself, however, virtualization is far from sufficient, and more work is needed to demonstrate the capabilities of virtualization-based solutions in the area of critical infrastructure. Indeed, for very small processing platforms that lack hardware support for e.g. memory protection, virtualization by itself may be too computationally heavy, and in that case other techniques such as software fault isolation (SFI) may be more appropriate.
The aim of this activity is to explore how virtualization-based techniques can be used to meet the demands of current and future SCADA/critical infrastructure platforms, regarding security, trustworthiness, and dependability. These are the primary concerns. Secondary concerns, but equally important for industry acceptance, is to meet requirements concerning functionality, real time performance, and cost, and to transfer outputs of the project in terms of know-how, designs, requirements, and code to industry and society.
Recent related publications
A2: Wireless Communication
Leader: Ragnar Thobaben
In this activity, we address the wireless security issues in critical infrastructures. We will adopt concepts from physical-layer and information-theoretic security and develop new secure wireless communication algorithms, protocols, and concepts. Even though the general concepts studied in this project are applicable to wide range of application scenarios, we will focus our studies to the demands of wireless SCADA system infrastructures. The performance of selected algorithms and concepts should be evaluated with the help of wireless testbed activities.
The purpose of this activity is to demonstrate that physical-layer security techniques are a powerful means to complement conventional security features of wireless SCADA system infrastructures in order to improve the resilience against attacks in the wireless domain (e.g., eavesdropping, jamming, impersonation), to reduce the security overhead resulting from heavy-weight encryption, and to improve the overall security performance. To reach this goal, we will focus on three aspects of physical-layer security: physical-layer authentication, wireless secret key generation and distribution, and jamming resilient wireless infrastructures.
Recent related publications
A3: Communication and Computation Infrastructures
Leader: György Dán
The purpose of this thrust of work is to develop secure and resilient algorithms and protocols for SCADA communication and computation in shared environments. The algorithms and protocols will leverage knowledge of the physical processes monitored and controlled, and the computations to be executed in order to achieve the best trade-off between performance, cost and security. We will focus on three areas: secure communication protocols emerging SCADA application scenarios, (ii) resilience to denial of service attacks, and (iii) we secure computation on untrusted computing platforms.
Recent related publications
A4: Resilient Control of Cyber-Physical Systems
Leader: Henrik Sandberg
In this activity, we address resilient control issues in critical infrastructures. We will adopt concepts and methods for cyber-physical systems in the study of reliability, safety, and security of critical infrastructures. For the analysis of the cyber components, this activity will heavily rely on and interact with the CERCES activities on embedded devices, wireless devices, and communication infrastructures. However, this activity has a strong focus of the physical aspect of the critical infrastructures, and will therefore take a more holistic view. Based on the vulnerability assessments and impact analysis made, we will develop detection and control algorithms that will improve the resilience of the infrastructure. The performance of selected algorithms and concepts should be evaluated with the help of the CERCES testbed.
The main goal of this activity is to develop control and monitoring algorithms to ensure resilient operation of critical infrastructures, such as smart grids and traffic systems. To achieve these goals, we will first develop modeling tools that are able to capture the essential behavior of both the cyber and physical components. Based on these, we will be able to perform a holistic vulnerability and impact analysis that serve to identify critical areas in the infrastructure. We can then design application-layer intrusion detection systems that can be incorporated in novel resilient control architectures that are able to encapsulate and attenuate malicious actions.
Recent related publications
