Secure control systems
Control engineering has traditionally developed theory and practice where certain properties of the cyber and physical world are assumed to have negligible impact on the resulting control performance.
For example, it has commonly been assumed that control design can be separated from the underlying communication system design. Given the continued convergence of the information sciences, and the emergence of large-scale networked control systems, we can no longer afford to rely on such assumptions. In fact, a central thesis in our work is that new important constraints in control design have emerged with respect to security, privacy, and information access. Therefore, it is urgently necessary to elucidate the impact of these limitations in the overall performance trade-offs in control systems.
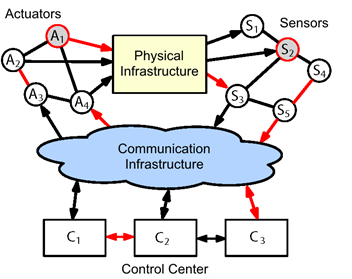
Specifically, we address the following challenges:
(A) Security. Cyber security in control systems is a rapidly evolving and increasingly important field and, presently, even the quantification of security in this domain is not well understood. The practical motivation comes from concerns that malicious attackers can stage cyber-attacks against large-scale networked control systems, such as critical infrastructures, with devastating societal impact. In response to this, we develop security metrics to localize weaknesses, and develop monitors and controllers resilient against large classes of malicious attacks.
(B) Privacy. The inclusion of privacy constraints in control design is another swiftly developing theme in control systems. The motivation comes from networked control systems where subsystems require control services from a central entity. The constraints arise because the subsystems do not desire to reveal certain private information, but yet need to give up some to obtain relevant feedback signals. In response to this, we develop novel monitoring and control techniques that take privacy constraints into account.
(C) Information. Entropy and mutual information are fundamental notions in both information theory and physics. Historically, these notions have received much less attention in control theory, despite their important role. Though they have been used to study stabilization over quantized channels, we use entropy and mutual information as tools for bounding general control performance criteria, in a manner reminiscent of their use in physics.
Much of the above work is conducted within the framework of the Center for Resilient Critical Infrastructures (CERCES), which is coordinated by Henrik Sandberg and also involves KTH faculty in the areas of communication networks, information theory, and theoretical computer science.
